
In the last quarter of 2018 organisations spent more than US$10 billion (NZ$14.7 billion) on cybersecurity – the highest levels ever, according to Canalys estimates.
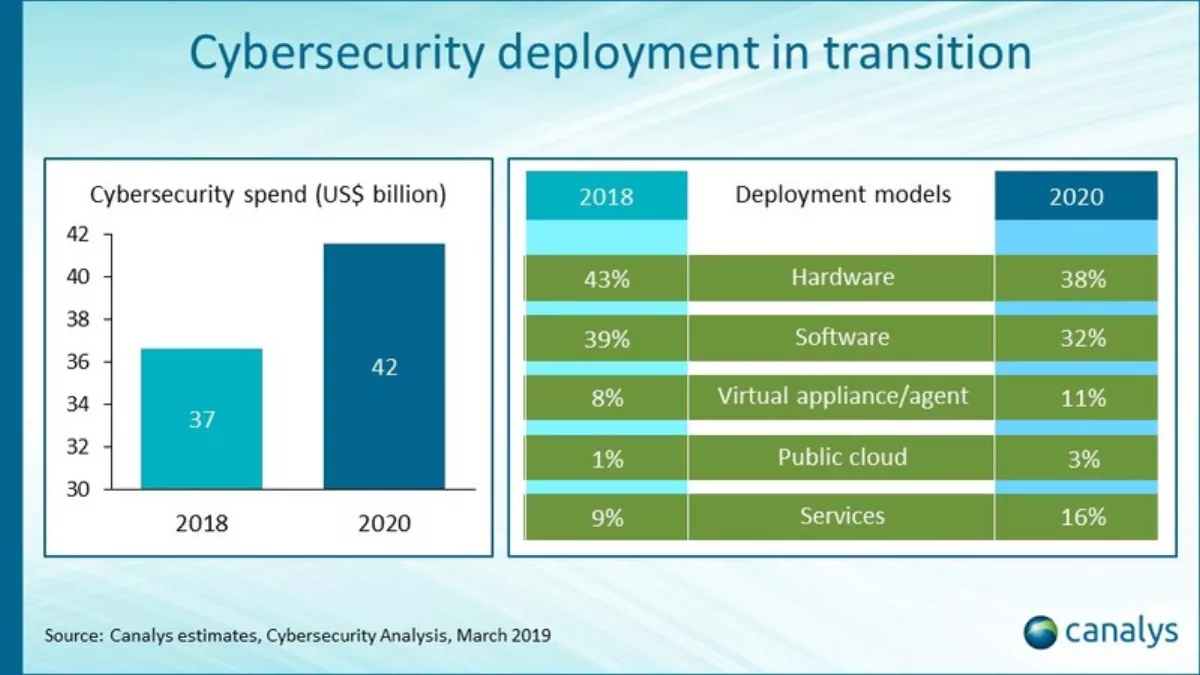
In 2018, total cybersecurity investment reached US$37 billion (NZ$54.3 billion). That number is expected to exceed US$42 billion by 2020.
But as spend continues to increase, cybersecurity only represents 2% of total IT expenditure, even as organisations increase protection against malicious threats and keep in line with data compliance regulations.
“Over the next two years, the transition in cybersecurity deployment models will accelerate. Customers are changing their IT buying behaviour, with the adoption of public cloud, and flexible consumption and subscription services,” say Canalys Principal Analyst Matthew Ball.
Canalys data also shows that in 2018 traditional hardware and software deployment accounted for 82% of the cybersecurity market. The remaining 18% was deployment of virtual appliances and agents, procurement through public cloud marketplaces and subscriptions to cybersecurity as a service.
Canalys names Cisco, Palo Alto Networks, Barracuda and Check Point as some of the top cybersecurity vendors.
“The leading cybersecurity vendors have embraced new deployment models, with each in the process of transitioning their businesses to more subscription-based revenue and increasing transactions via cloud marketplaces,” says Canalys Research Analyst Ketaki Borade.
“Cisco, Palo Alto Networks, Barracuda and Check Point are also the top cybersecurity vendors on the leading public cloud marketplace, AWS Marketplace, selling their virtual offerings on a per hour and annual basis. This is still a small part of their overall business, but is the fastest growing area.”
“Barracuda Networks, Trend Micro and F5 Networks also have a strong presence on cloud marketplaces, highlighting their early move to adopt new deployment models.
In Q4 2018, Cisco remained the overall worldwide market leader, growing its share from the previous year to just under 10%. Palo Alto Networks grew faster but remained in second place with 7%. Check Point, Fortinet, IBM and Symantec each had 6% market share in Q4. Overall, the top 10 cybersecurity vendors collectively represented 53% of shipments during this period, with the next 20 accounting for 21%.
Cybersecurity quarterly estimate and forecast data is taken from Canalys' Cybersecurity Analysis service. Estimates include network security, endpoint security, web and email security, data security and vulnerability and analytics security. The subscription service tracks the transition of deployment options from hardware and software to services, public cloud workloads and virtual appliances/agents by channel and end user size.
