
A worldwide spate of spam emails claiming there is a bomb in the recipient's building is almost certainly a hoax, but some national cybersecurity agencies are still asking those recipients to call their local authorities.
The Australian Government's Stay Smart Online website and New Zealand's Computer Emergency Response Team (CERT) posted bulletins about the emails last week.
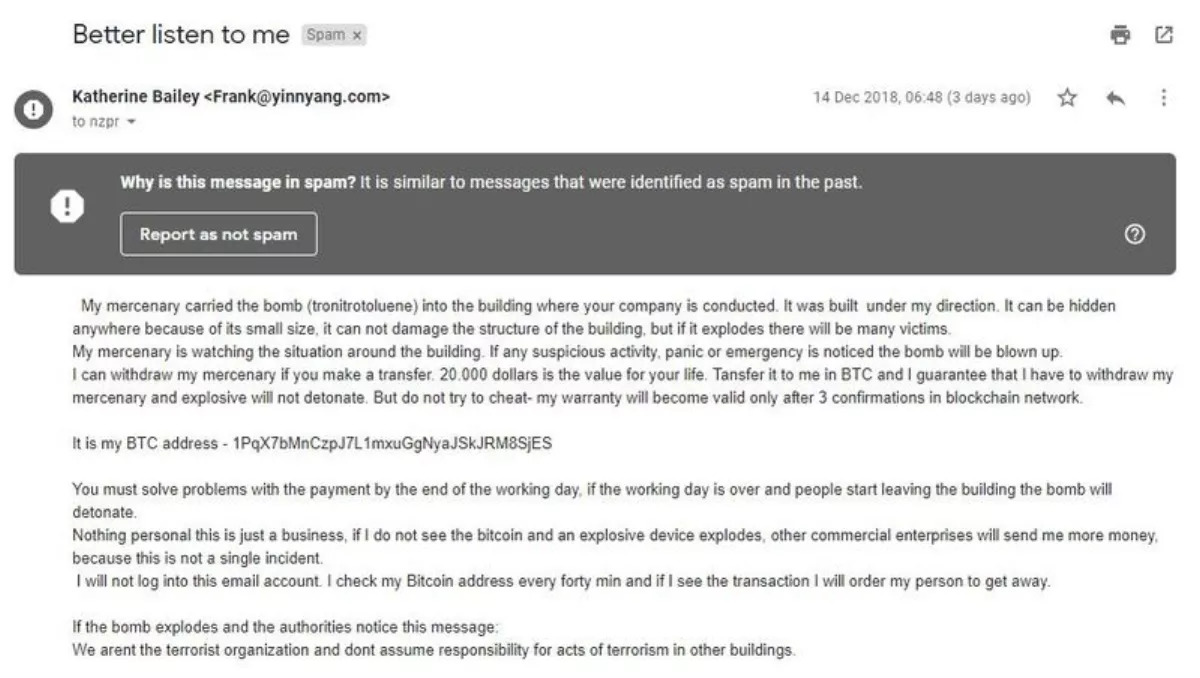
CERT NZ says the emails claim an explosive device is hidden in the recipient's office. Unless the recipients pay the ransom in bitcoin, the device will be detonated.
Newer variations of the emails claim that acid will be thrown at the recipient if they do not pay the ransom.
In a blog, Cisco Talos' Jaeson Schultz says the sender's claims are ‘completely false', but they have caused a lot of damage as organisations have been forced to evacuate and call upon law enforcement.
“Talos has discovered 17 distinct Bitcoin addresses that were used in the bomb extortion attack. Only two of the addresses have a positive balance, both from transactions received Dec. 13, the day the attacks were distributed. However, the amounts of each transaction were under $1, so it is evident the victims in this case declined to pay the $20,000 extortion payment price demanded by the attackers,” writes Schultz.
Here's a sample of one that landed in TechDay's editorial inbox:
 Schultz says that multiple IPs identified in the bomb threat scam are the same ones that were behind a flood of sextortion emails earlier this year.
Schultz says that multiple IPs identified in the bomb threat scam are the same ones that were behind a flood of sextortion emails earlier this year.
“What makes these particular extortion messages unique from other extortion scams we've monitored is that, previously, the attackers threatened only the individual — the attackers would threaten to expose sensitive data, or even attack the recipient physically, but there was never any threat of harm to a larger group of people, and certainly not the threat of a bomb.
“While this is likely to be an opportunistic scam, New Zealand Police are working to confirm the validity of the threats until confirmed otherwise. If you receive the email, we encourage you to contact police,” says CERT NZ.
Schultz claims that the criminals behind the emails are willing to come up with any threat in order to fool people.
“At this point, we have seen several different variations of these emails, and we expect these sorts of attacks to continue as long as there are victims who will believe these threats to be credible, and be scared enough to send money to the attackers. Talos encourages users not to fall for these schemes and — above all — DO NOT pay extortion payments. Doing so will only confirm for the attackers that their social engineering approach is working, and victims' money goes directly toward facilitating additional attacks,” Schultz says.
CERT NZ also warns anyone who received the email: • Do not respond or try to contact the sender. • Do not pay the ransom or take any further action until you have spoken to police. • Keep the email as evidence to pass to police.
